Even the best equipped SOC teams bleed time on two fronts:
Tier 1 analysts click on false positives all day.
Tier 2 analysts correlate logs, pivot across the tool, and report them all the way after business hours.
“Tier 1 and Tier 2 are the main tasks within the Security Operations Center, so everything you can do to promote increased efficiency is a big positive,” says Philip Beck, former SOC manager and current D3 sales engineering director at the recent Morpheus AI workshop. Our new white paper, “Fully automates the L1 & L2 SOC OPS. This is how we do it,” explains the architecture behind those wins. Grab it now and dig deeper into what these L1 and L2 tasks are and why they are the perfect targets of autonomy.
Download the white paper →
Why Full-Stack Automation Beats Fragmental Fixes
A 2025 Gartner survey of Cybersecurity Leaders found that organizations have 43 cybersecurity tools in their product portfolio, with 5% reporting that they have over 100 tools. Toolsplore manually stitches together context, a “ticket fling” escalations to analysts, and eventually burns out as they chase the ghost.
Fragmented automation, like Legacy Soars, only adds to complexity with vulnerable scripts and endless playbook maintenance. A true autonomous SOC solution requires you to sit on the entire security stack and integrate all your signals without ripping and replacing already reliable tools. Morpheus ai supports the SOC team:
Efficiency and speed. The 3.5-hour phishing survey case drops to less than 2 minutes when Morpheus handles all enrichment, queries, and correlations in parallel. Your team will crush your response time by 315 times faster. Scalability. Automation allows MSSPs to add tenants. Alternatively, the company can add business units and new use cases without adding personnel. Cost management. “Reducing triage invoices will unlock new talent and tools budgets,” said Pierre Nojaim, director of cybersecurity services at D3 at a recent workshop. By fully automating the work of L1 and L2 SOCs, you can reinvest these six-figure savings into aggressive security measures and ponder your team. Analyst retention. Removing “Hash Check Painful” reverses the burnout that drives a two-year turnover cycle.
What are L1 and L2 SOC tasks?
In modern SOCs, Tier-1 (L1) work is a fast-paced triage where alerts are instantaneously generated. Analysts intake and normalize events from all tools, verify the health of the connector, perform rapid hash/IP/URL reputation checks, and decide whether to close or escalate. Morpheus folds each of those chores into a pre-processing pipeline, streams alerts to the graph model, stacks on-the-spot concentrations, and automatically rejects about 95% of the alerts within two minutes.
Tier-2 (L2) work begins when something survives L1. Investigators should correlate different signals, reconstruct timelines, explode suspicious files, swipe the entire log to see the extent and root cause, and draft a containment plan. Morpheus replicates its detective efforts with its deep research framework, firing dozens or hundreds of vertical and horizontal queries at once, bringing the findings back to the same evidence graph, reducing the usual 3.5 hours of manual investigation, and meeting AI-generated playbooks and incident priorities.
Inside the Morpheus engine
Morpheus AI was built to act like a world-class analyst who never sleeps, running the entire research and triage workflow with superhuman speed and accuracy. How does this work:
Intake and Uniform Data Model
Start by connecting to everything in the security stack. Morpheus’s 800+ AI-first integrations help you intake alerts and data from EDR, NDR, Cloud, IAM and more. Tools or platforms with APIs or webhooks can be integrated with Morpheus. Instead of storing terabytes of data, Morpheus consumes alerts and metadata, normalizing them to a graph-based schema that stores the relationships between tools and time. Device Asset Tags, Business Criticism, User Risk Scores, and Threat Intel Feed are merged on the fly, providing a 360-degree view for subsequent investigation steps.
Deep Research Framework (DRF)
Once the alert is taken, Morpheus’ deep research framework begins a large-scale, parallel investigation. It behaves like a Tier 3 analyst and runs hundreds of queries across the stack in seconds. This is a time-consuming process for human analysts.
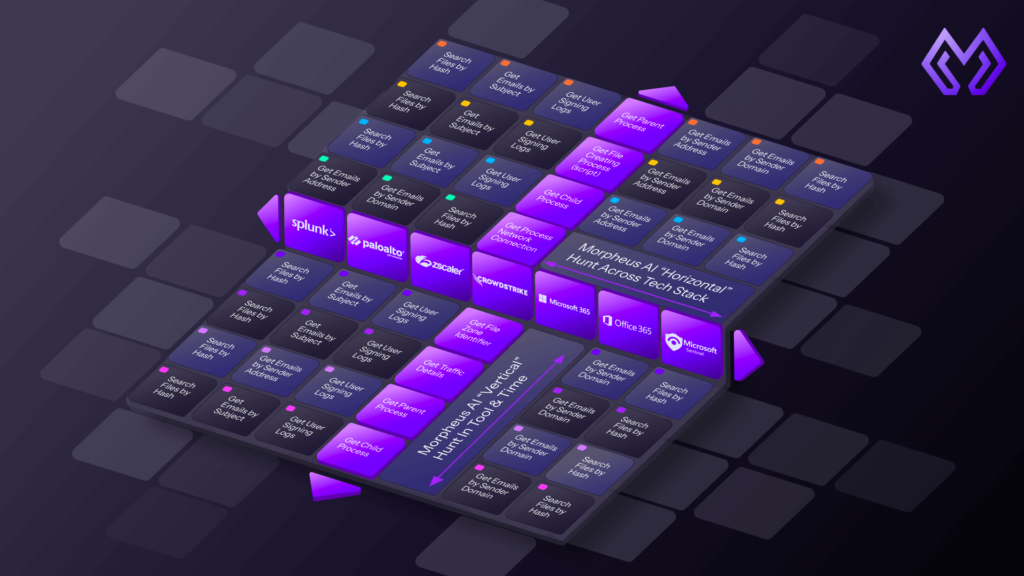
Vertical analysis: Explore process trees, registry keys, and raw telemetry to understand the underlying causes. Horizontal analysis: Distribute fans across all integrated tools, from firewalls to email gateways, linking relevant signals to a single, cohesive attack story.
All investigation steps are written back as a transparent, auditable YAML playbook. There’s no need to worry about black box AI. Morpheus gives you transparent, explainable logic that analysts can review and refine.
Noise Kill Automation and Continuous Learning
Alert fatigue is an effective SOC enemy. Morpheus’ pre-processing playbook autonomously triages 95% of incoming alerts within two minutes, instantly dismissing obvious false positives and low fidelity signals. The system learns from analyst feedback. When analysts validate an incident, their thumb/down decision teaches AI, continually improves its logic and reduces the false positive rate without writing new rules.

Cross-Stack Incident Response Priority Score (IRPS)
Forget the common “high, medium, low” labels. Morpheus calculates a Numeric Incident Response Priority Score (IRPS) that blends multiple factors for prioritization of True, At-A-Glance.
Threat Confidence: Reputation of IOCs, malware families, and known exploits. Business Impact: Asset Importance, Data Sensitivity, and Potential Blast Radius. Mitigation status: whether the user or endpoint is already included in another tool. Historical background: Previous occurrences of similar IOCs or TTPs in environments.
The result is a fully sorted queue, with the top items always being the most urgent threat.
Tier-3 compatible queue
Because noise is filtered and prioritized, Morpheus provides a column of confirmed incidents to senior analysts. Each incident package is tier 3 compatible and completes the following:
Complete attack timeline and link analysis graph. Root cause analysis and recommended repair steps. A pre-built containment plan. Take proactive action for human recognition.
Analysts don’t start from scratch anymore. They start with the answer.
Task-Level Time Savings: SOC Analyst vs. Morpheus AI
Increased efficiency is transformative. Morpheus completes a typical fishing survey that takes 3.5 hours in less than two minutes, with expert human analysts.
Task Expert SOC Analyst Morpheus AI Alert Validation and Ticket Logging 10min 5S Time Stamp Correlation Platform 10min 5S Email Content and Header Analysis 10min 5min 5min 5S Extract Malicious URLs from Firewall Log Outbound Connection 15min 5min 5min Network Traffic Analysis WHOIS Information Search 5min 5S URL Redirection and Destination Verification Number of minutes per Incident
Ready to see L1 and L2 run on autopilot? 
Achieve Fortune 100 levels of resilience without adding more personnel or ripping tools already invested in. Morpheus provides 100% alert coverage, 315 times faster investigations, and evidence of transparent audit responses for any action. Focus on the analyst and get back to the weekend.

For more information, download the white paper: “Fully automate L1 & L2 SOC OPS” →
Do you need to see it with your own data? Book a live demo and discuss SOC automation challenges and automation wish lists.
The way Morpheus AI automates the entire L1 and L2 pipeline was first introduced in D3 Security.
***This is the D3 Security Security Blogger Network Syndicate Blog, created by Shriram Sharma. Read the original post at https://d3security.com/blog/how-morpheus-ai-automates-the-the-l1-l2-pipeline/




